Identity Target Attacks
Security Device Management
Cybersecurity resilience relies on every layer. In your network, various security solutions—from firewalls to antivirus—are deployed. Cyberspace IT® enhances your defense with thorough Security Device Management. We update and optimize your security devices, ensuring the latest patches and best practices adherences to keep your defenses robust against evolving threats.
Strengthen Network Security
Stay ahead of targeted attacks with Cyberspace IT®‘s Risk-based Vulnerability Management. By proactively addressing vulnerabilities, organizations fortify defenses. Regular OS and application updates shield against drive-by downloads and software vulnerabilities, common ransomware entry points. Our approach prioritizes your greatest risks, streamlining patch management for a secure, up-to-date digital environment.
Automated Threat Response
Combat ransomware and elevate your security posture with Cyberspace IT® Managed Firewall services. With block rules on next-gen firewalls, we limit threats and provide indicators of compromise, optimizing firewall appliances for robust infrastructure health and tailored next-gen firewall capabilities.
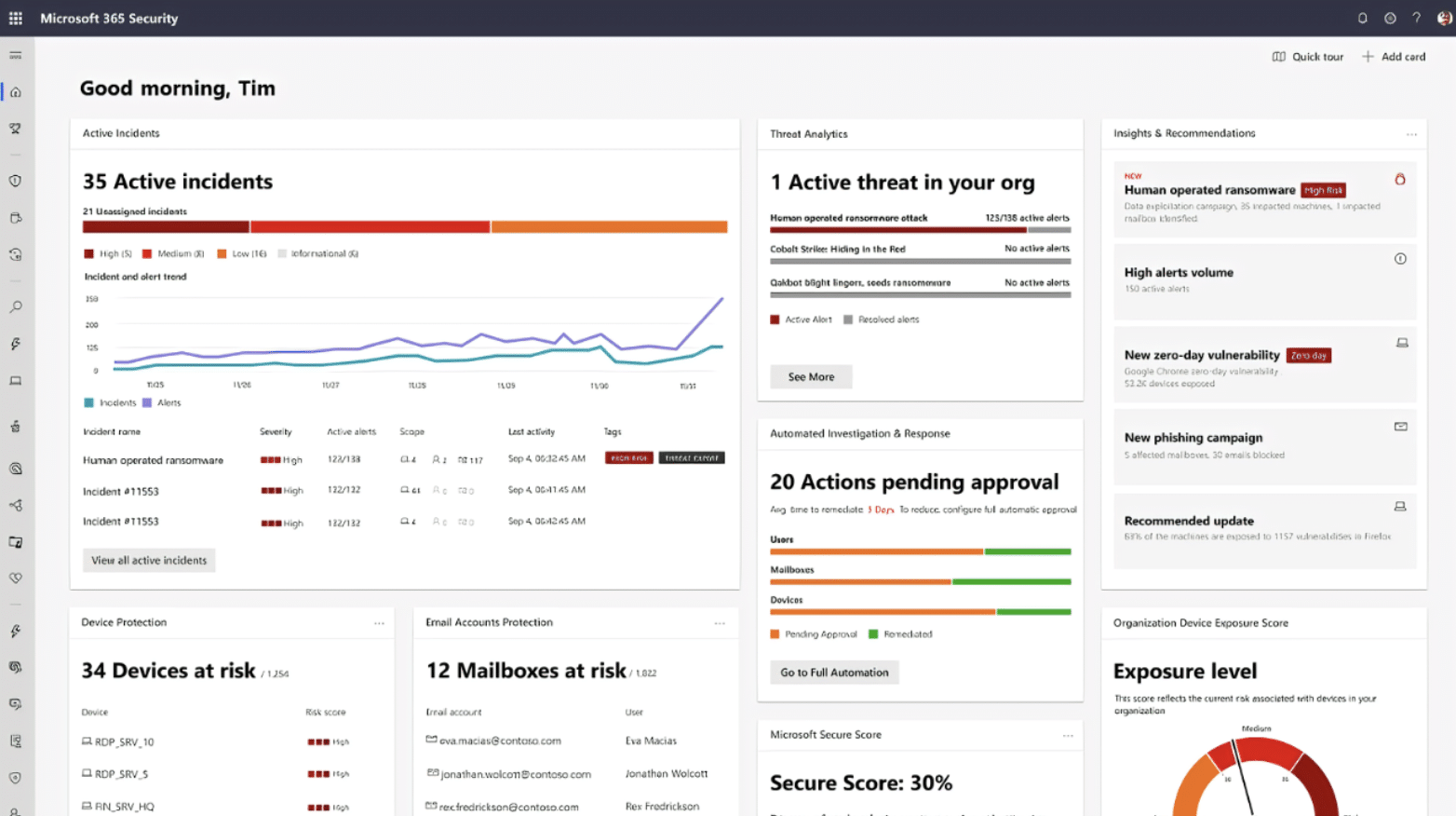
ADVANCED THREAT DETECTION MECHANISMS
Our Cyber Exposure Monitoring service is a vigilant guardian against Dark Web threats. Continuously scanning for leaked credentials, we proactively thwart cybercriminal access. Delving into the Dark Web, we unveil external threats, empowering you to preemptively respond to emerging threats, and stay ahead of potential breaches.
Proactive Threat Hunting
Our expert threat hunting actively identifies and eliminates targeted malicious activities. SpaceSOC® MDR service enhances this by leveraging insights from other clients’ networks, fortifying collective efforts. With the aid of machine learning models that detect anomalies, we ensure a resilient defense against the ever-evolving landscape of targeted threats.
Safeguard Against Insider Threats
Cyberspace IT® safeguards your organization by crafting security policies and use cases to unveil any misuse of company resources. Our Incident Trends Dashboard provides a comparative analysis, offering insights into your policy compliance, incident types, and frequency in comparison to real-world data and similar vertical organizations.

